TCP (Transmission Control Protocol)
It is used in the transmission of data over networks.
It is responsible for ensuring reliability during transmission. Means:
- All the packets reach the destination, that is no packet is lost.
- There is no such delay that would affect data quality.
- All data packets are reassembled in order.
TCP labels its packets (they are numbered). It also makes sure they have a deadline to reach the destination (time-out).
It performs 3 way handshake for reliability.
It uses IP and numbers (ports) provided by the device it is working on to identify where it is receiving and sending packets and for which service.
For example, web browsers uses port 80 for TCP, email uses port 25. The port number is often coupled with the IP address for a service, e.g. 192.168.66.5:80
Packet Structure:
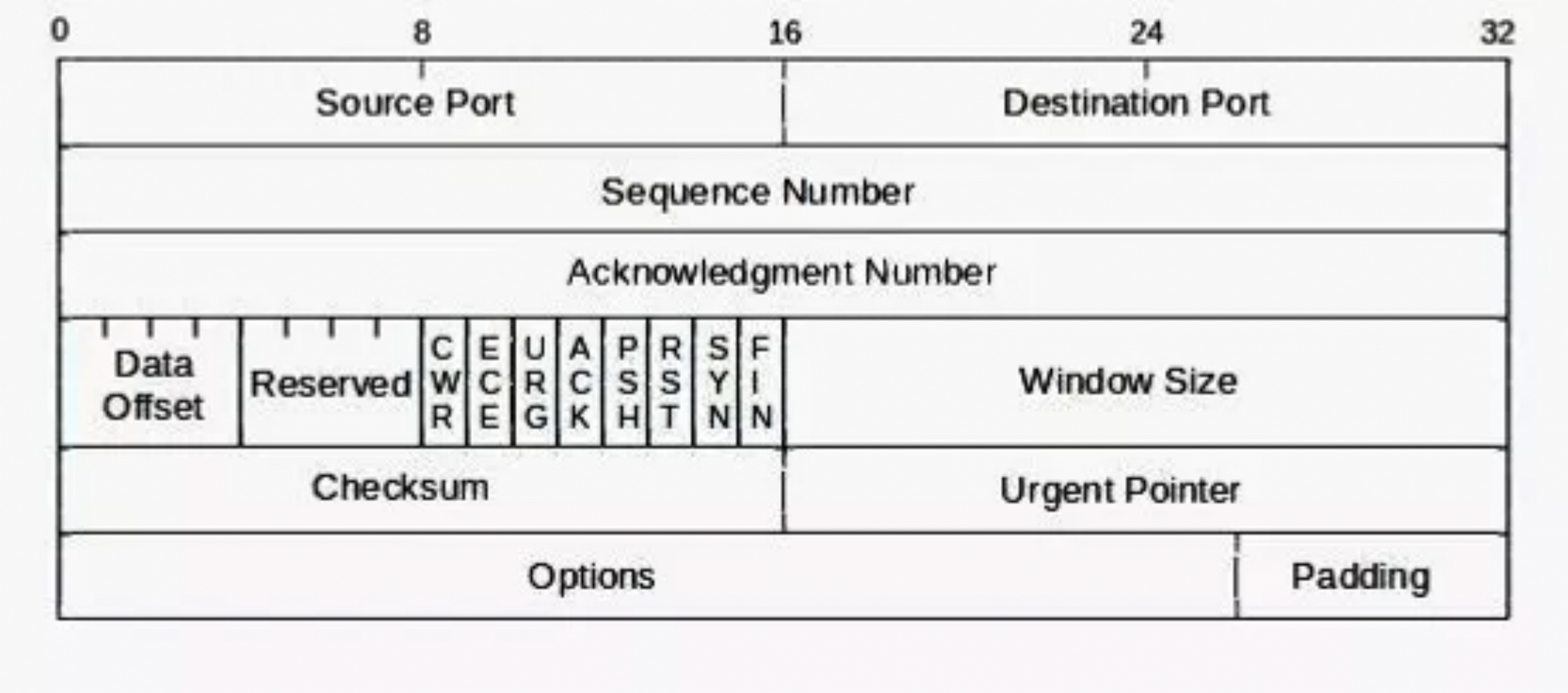
Row 1
- Source Port / Destination Port: These fields determine what port the communication came from (source) and where it is going (destination).
Row 2
- Sequence Number: The sequence number is generated by the source machine's TCP stack and is used to make certain that packets are arranged in the proper sequence when they arrive.
Row 3
- Acknowledgement Number: This is an echo of the Sequence Number sent back by the receiving system. It basically says, "I received the packet with the Sequence #." In this way, the sender knows that the packet arrived. If the sender does not receive an Acknowledgment Number back in a fixed amount of time, it will resend the packet to make certain the receiver gets the packet.
3-way Handshake:
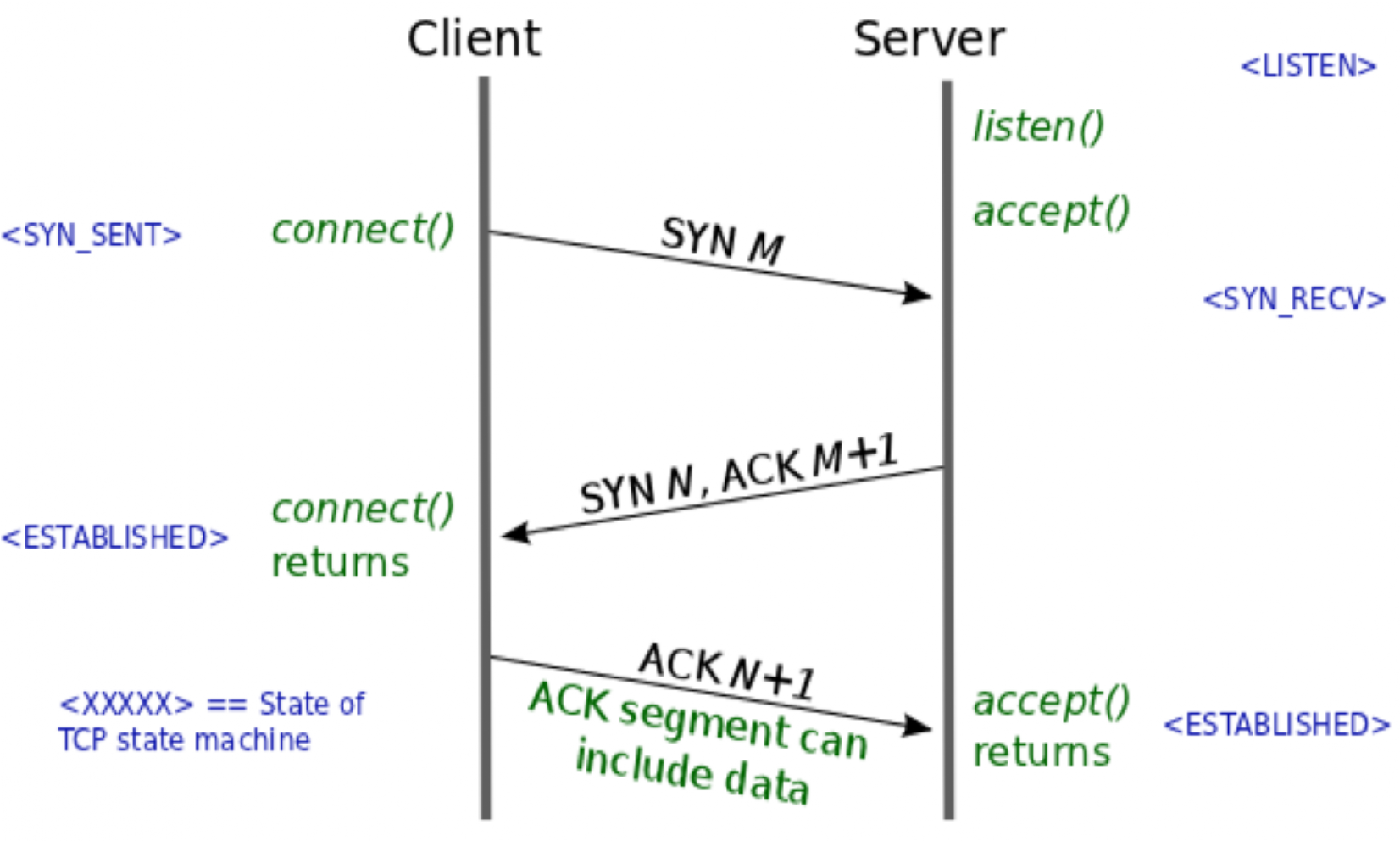
In this way, TCP is reliable (in contrast, UDP does not do this and is therefore unreliable).
Row 4
- Data Offset - Header Length field
- Flags (Skipping to 8 bits near the middle of Row 4)
By default flags are set to 0 to activate them they are set to 1. - CWR and ECE : These TCP flags are used together with two flags in the IP Packet's header (ECT and CE) to warn senders of congestion (clog) in the network thereby avoiding packet drops and retransmissions.
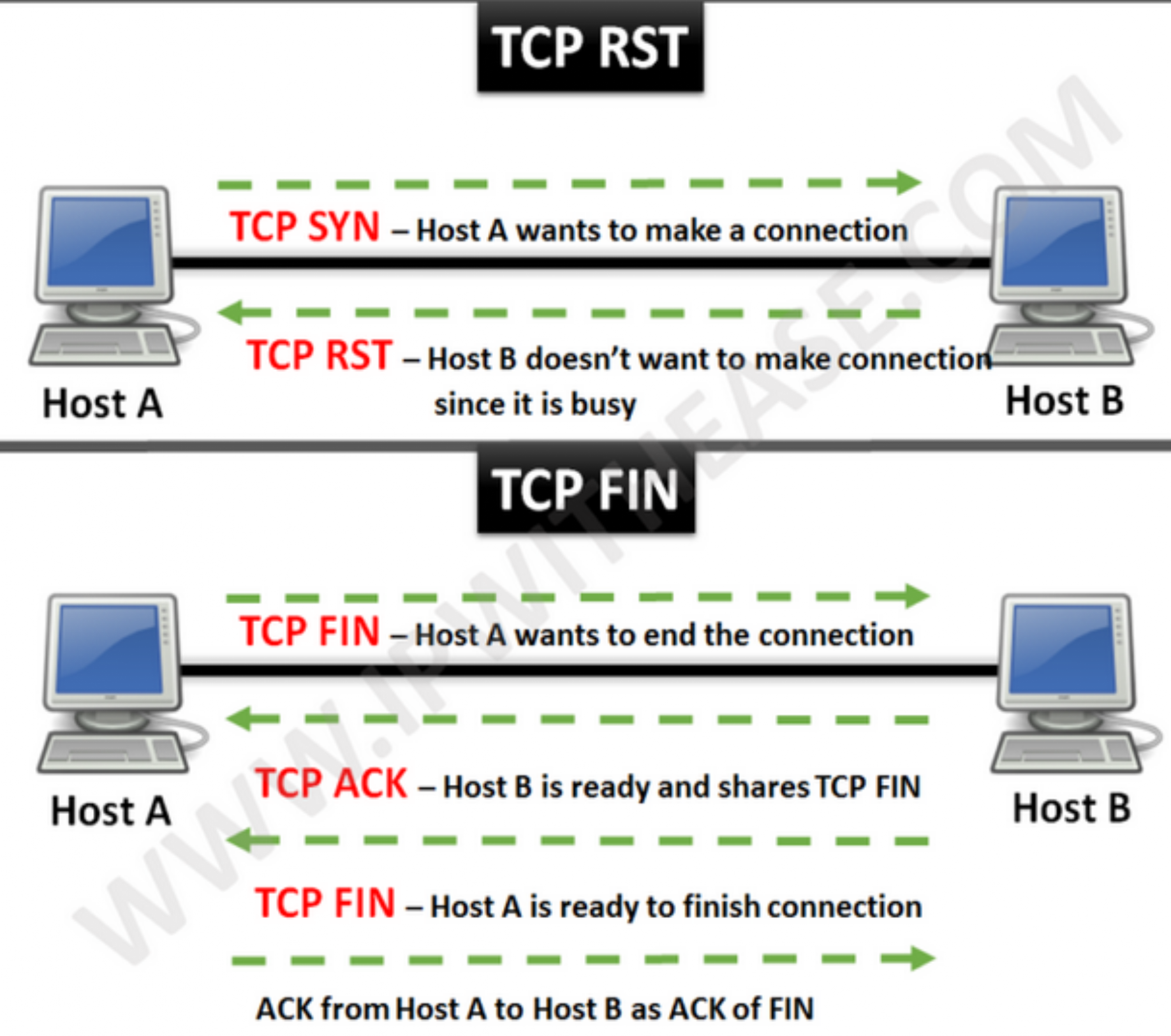
- SYN: Synchronizes sequence numbers to open of a new connection
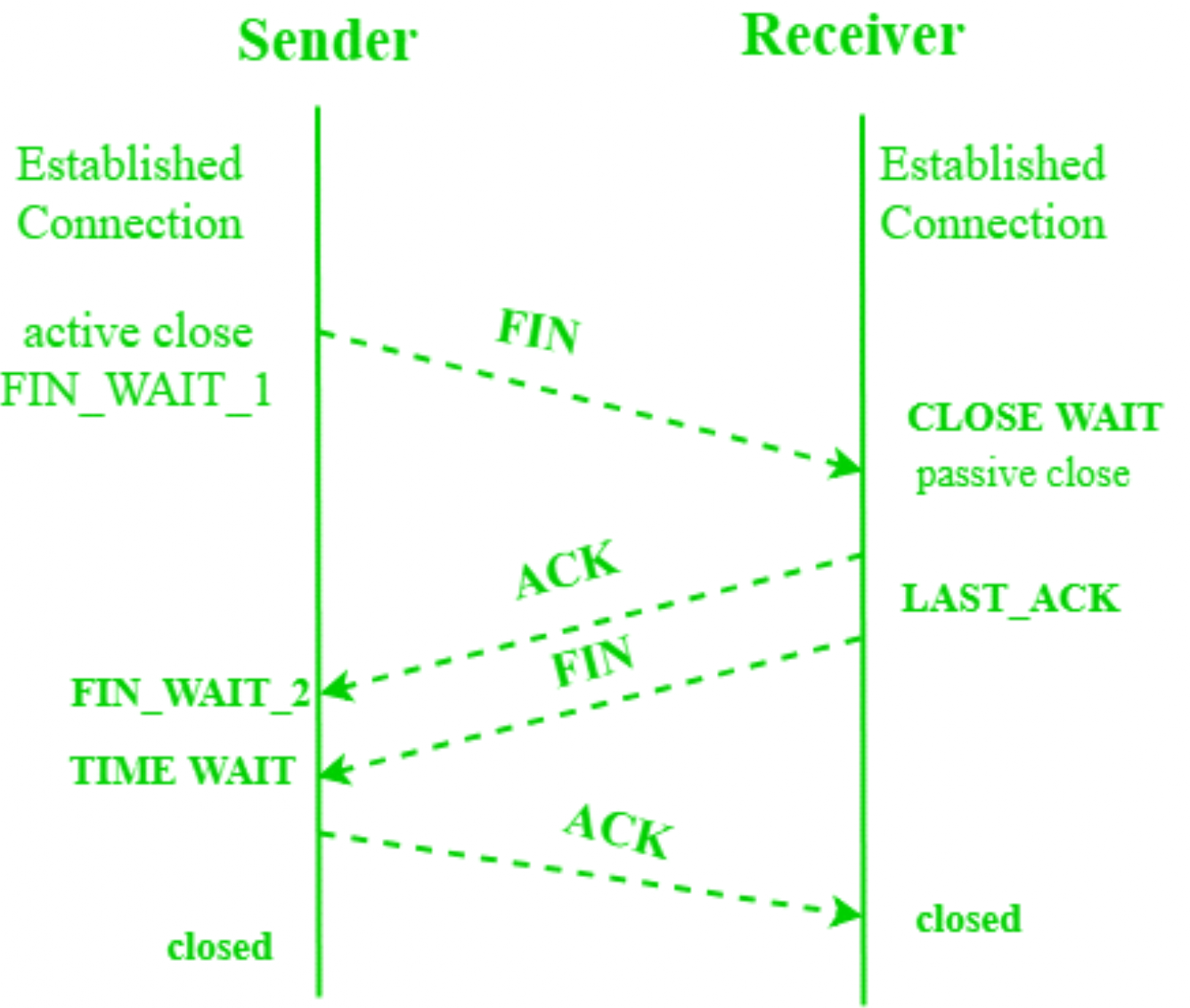
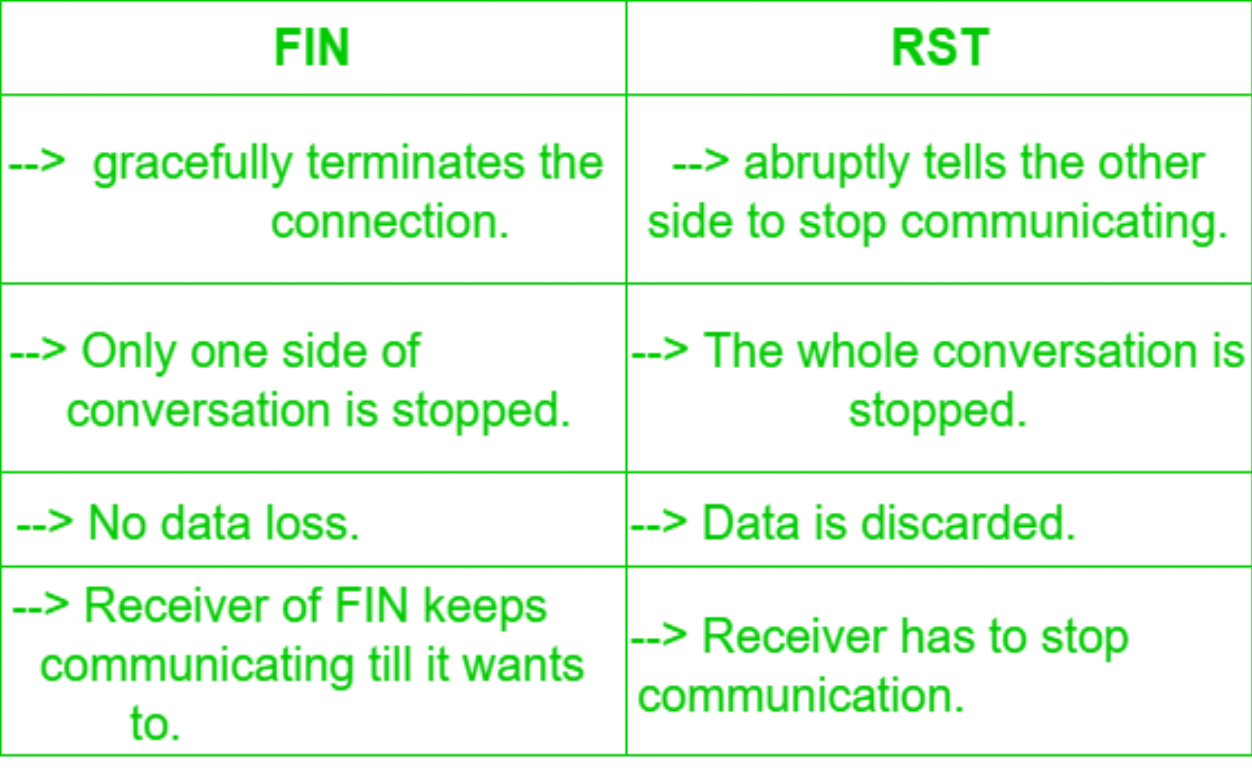
- FIN: It is used to request for connection termination i.e. when there is no more data from the sender. This is the last packet sent by sender. It frees the reserved resources and gracefully (softly) terminate the connection.
- ACK: The acknowledgment of a packet. It Indicates that acknowledgement number is valid.
- RST: It resets the connection.Connection is closed forecly (hard) and it is usually used to communicate that the packet has arrived at the wrong port or IP.
PSH: Indicates to push the data past the buffer to the application as soon as possible.
Buffer!, What ?
A buffer is a chunk of memory that stores packets temporarily when there is too much data sent to a network interface (either generated by the host, or in the case of a switch or router, received from a different interface).
Packets get dropped if the buffer memory is full.
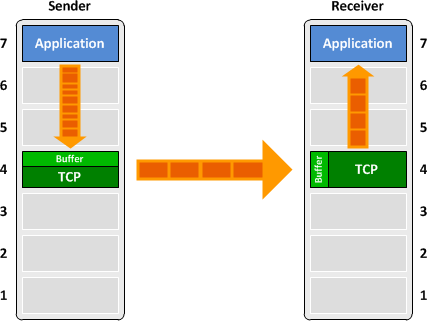
Understanding The PUSH (PSH)
Transport layer by default waits for some time for Application layer to send enough data so that the number of packets transmitted on network minimizes which is not desirable by some application like interactive applications (chatting).
Similarly at receiver end Transport layer buffers packets and transmit to Application layer if it meets certain criteria.
This problem is solved by using PSH. Transport layer sets flag PSH = 1 and immediately sends the segment to network layer as soon as it receives signal from application layer.
At receiver's end transport layer (on seeing PSH = 1) immediately forwards the data to application layer.
In general, it tells the receiver to process these packets as they are received instead of buffering them.
- URG: Indicates that the following data is urgent.If URG = 1 flag is set data is forwarded to application layer immediately even if there is more data to be given to application layer. It notifies the receiver to process the urgent packets before processing all other packets.Used in older protocols like Telnet.

- Window Field or Window Size: It specifies the size of the sender's receive window (buffer space available for incoming data).This is the way that TCP manages flow control.This field varies from OS to OS.
Flow control?
TCP manages data buffers and coordinates traffic so its buffers will never overflow. Fast senders will be stopped periodically to keep up with slower receivers.
Row 5
- Checksum: It indicates whether the header was damaged in transit and check for errors. Basically, it is an integrity checker.
- URG Pointer: This field points to the last byte of the sequence number of urgent data. The URG flag must be set in conjunction to activate this field.
- Options: Like the IP header, the TCP header has an options field that can be used if necessary and it is varying length.
- Padding: The padding is necessary to bring the TCP header to a multiple of 32 bits.
UDP (User Datagram Protocol)
It is unreliable because it uses a simple connectionless communication model.
It is often used in video conferencing applications or computer games that are made specifically for real-time performance.
To achieve higher performance, the protocol allows individual packets to be dropped (with no retries) and UDP packets are received in a different order than they were sent.
In UDP, checksumming is optional, as opposed to TCP where checksums are mandatory.
Because UDP is limited in capability compared to TCP, its headers are smaller.
Packet Structure:
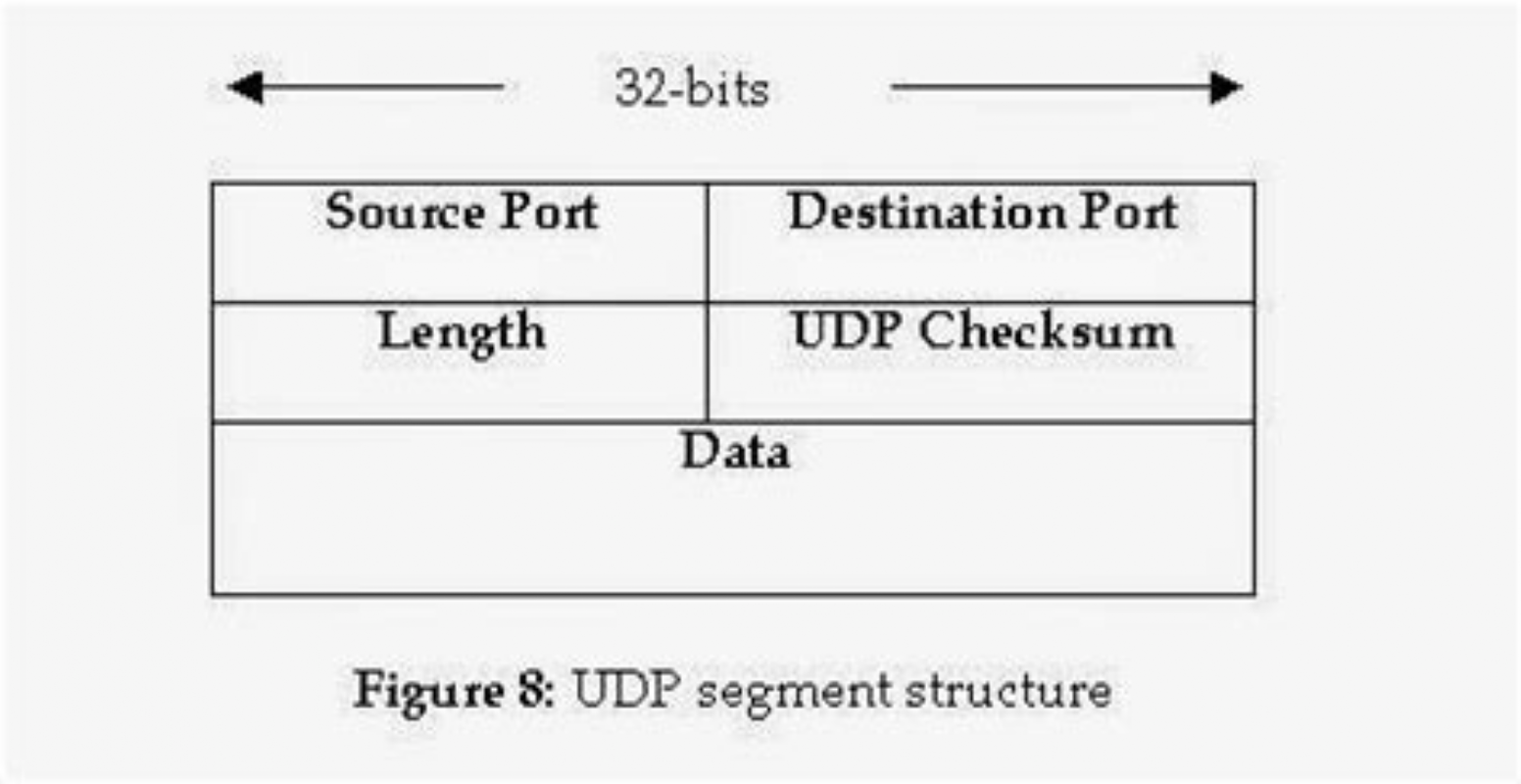
- Source Port: The source UDP port number of the sending device.
- Destination Port: The destination UDP port number is the communication endpoint for the receiving device.
- Length of data: This field represents the total size of each datagram, including both header and data.
- UDP checksum: Allows receivers to cross-check incoming data for any corrupted bits of the message.